InviZible Pro **BETA**
| AppID: | pan.alexander.tordnscrypt |
| Author: | Oleksandr Garmatin |
| License: | GPL-3.0-or-later |
| Donation: | Webpage |
| InRepoSince: | 2019-12-07 |
| LastRepoUpdate: | 2026-02-21 |
| LastAppUpdate: | 2026-02-20 |
| LastVersion: | 2.6.6 |
| Categories: | Internet, Security |
| APK source: | Github |
| Google Play: | Check if it's there |
Preserves privacy, prevents tracking, and provides access to restricted and hidden online content.
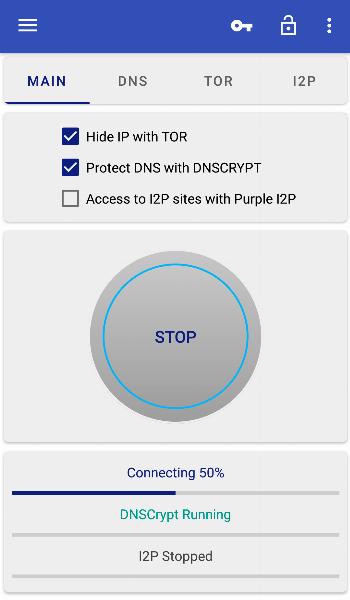
InviZible Pro combines the strengths of Tor, DNSCrypt, and Purple I2P to provide a comprehensive solution for online privacy, security, and anonymity.
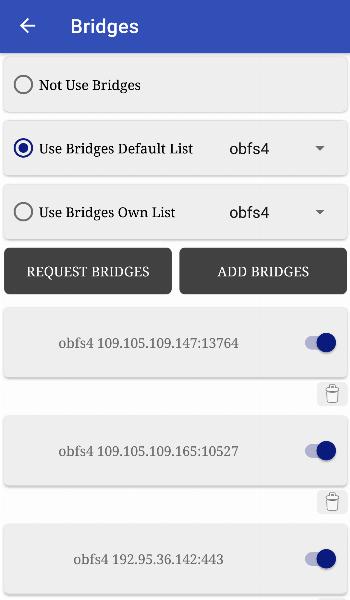
Tor is responsible for privacy and anonymity. It acts like an unlimited free VPN proxy, but does so in the most secure way possible. Tor uses military-grade encryption and routes your internet traffic through a network of volunteer-run proxy servers. This helps protect your identity and location by hiding your IP address. It allows you to browse the internet anonymously, access websites that are otherwise restricted, and communicate privately. Tor also allows access to websites hosted on the Tor network, known as "onion services" or dark web, which are not accessible through regular browsers.
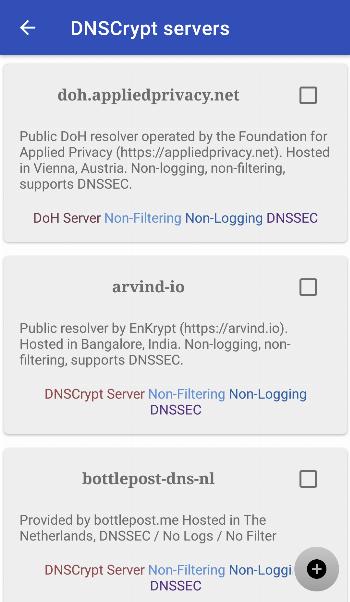
DNSCrypt is responsible for security. Every phone uses DNS (Domain Name System) when visiting online resources. But this traffic is usually not encrypted and can be intercepted and spoofed by third parties. DNSCrypt ensures that your DNS traffic is encrypted and secure. It prevents unauthorized access and tampering of your DNS queries, providing an additional layer of protection against surveillance and data interception.
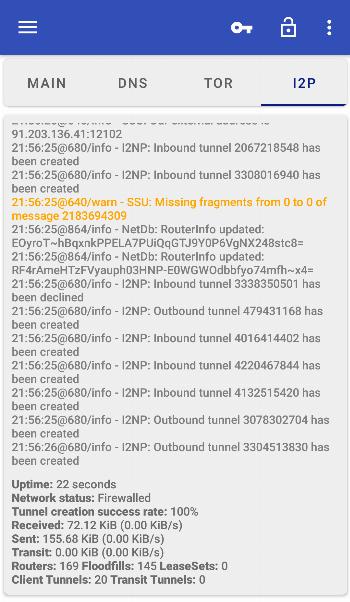
I2P (Invisible Internet Project) provides secure and anonymous access to internal I2P websites, chat forums and other services that are not available through regular browsers. You may know it as the deep web. It works by routing your internet traffic through a network of volunteer-run proxy servers, allowing you to hide your identity and location. I2P provides a secure and private online environment, making it a great option for those who value anonymity and privacy.
Firewall is a security feature that helps protect your device from unauthorized access and potential threats. It acts as a filter for incoming and outgoing network traffic, allowing you to control which apps can access the internet. By setting up firewall rules, you can choose to block or allow internet connection for individual apps. This helps enhance your privacy and security by preventing unauthorized communication and protecting your data while using your phone.
InviZible Pro can utilize root access, if available on your device, or use a local VPN to deliver internet traffic directly to the Tor, DNSCrypt, and I2P networks.
Core Features: ✔ Tor Network - Achieve full anonymity, bypass censorship, and access .onion sites securely ✔ DNSCrypt - Encrypt DNS queries to prevent ISP monitoring and manipulation ✔ I2P (Invisible Internet Project) - Secure and private decentralized networking ✔ Advanced Firewall - Restrict internet access per app and block unauthorized connections ✔ No Root Access Required - Works seamlessly on all devices without modifications ✔ Maintain complete privacy without a paid VPN - Stay anonymous for free ✔ Stealth Mode - Evade Deep Packet Inspection (DPI) and regional restrictions ✔ Free & Open Source - No ads, no tracking, no compromises
WhatsNew:
**InviZible Pro beta 2.6.6**
* Updated Purple I2P to version 2.59.0.
* Fixes and optimizations.